Knowledge / Continuous Threat Exposure Management
What is Continuous Threat Exposure Management?
Continuous Threat Exposure Management (CTEM) is a proactive cybersecurity framework that enables organizations to actively identify, assess, and mitigate security risks in real time. By continuously discovering, evaluating, and prioritizing threats, CTEM delivers comprehensive visibility into an organization’s attack surface, empowering security teams to stay ahead of emerging threats. For security leaders struggling with limited resources and growing threats, CTEM offers a structured, efficient approach to managing security exposure. It transforms security from a reactive firefighting exercise into a proactive strategy that anticipates and prevents threats before they can impact the business
For security leaders struggling with limited resources and growing threats, CTEM offers a structured, efficient approach to managing security exposure. It transforms security from a reactive firefighting exercise into a proactive strategy that anticipates and prevents threats before they can impact the business.
What Problem Does CTEM Solve
The global cybersecurity landscape is undergoing a transformation, characterized by threat actors who employ increasingly sophisticated and adaptive attack strategies. Security teams now find themselves caught in a perpetual game of catch-up, desperately trying to identify, assess, and mitigate emerging threats while managing an ever-expanding attack surface. In this new reality, CTEM emerges as a groundbreaking solution, addressing pain points that have long plagued enterprise security.
- 1. Lack of Real-Time Threat Visibility
Organizations often struggle to maintain real-time visibility into their threat exposure due to fragmented tools, siloed data, and the dynamic nature of cyber threats. CTEM provides continuous monitoring and assessment of the threat landscape, offering real-time insights into vulnerabilities, attack vectors, and potential risks.
- 2. Reactive Security Posture
Many organizations operate in a reactive mode, addressing threats only after they have been exploited, leading to increased damage and recovery costs. By continuously identifying and prioritizing threats, CTEM enables organizations to shift from a reactive to a proactive security posture, mitigating risks before they are exploited.
- 3. Overwhelming Volume of Alerts
Security teams are often inundated with a high volume of alerts, many of which are false positives or low-priority, leading to alert fatigue and missed critical threats. CTEM employs advanced analytics and automation to filter, prioritize, and contextualize alerts, helping security teams focus on the most critical threats.
- 4. Difficulty in Prioritizing Risks
With limited resources, organizations struggle to prioritize which risks to address first, often leading to inefficient allocation of security efforts. CTEM provides risk-based prioritization, helping organizations focus on the most significant threats based on their potential impact and likelihood of exploitation.
- 5. Inconsistent Threat Intelligence
Organizations often rely on disparate sources of threat intelligence, leading to inconsistent and sometimes conflicting information. CTEM integrates and correlates threat intelligence from multiple sources, providing a unified and consistent view of the threat landscape.
- 6. Compliance and Regulatory Challenges
Meeting compliance and regulatory requirements can be challenging, especially with evolving standards and the need for continuous monitoring. CTEM helps organizations maintain continuous compliance by providing ongoing monitoring, reporting, and documentation of their security posture.
- 7. Resource Constraints
Many organizations face resource constraints, including limited staff, budget, and expertise, making it difficult to manage their threat exposure effectively. CTEM automates many aspects of threat detection, assessment, and response, reducing the burden on security teams and allowing them to focus on strategic initiatives.
- 8. Complexity of Modern IT Environments
The complexity of modern IT environments, including cloud, hybrid, and multi-cloud setups, makes it challenging to maintain a comprehensive security posture. CTEM is designed to work across diverse and complex environments, providing a holistic view of threat exposure regardless of the underlying infrastructure.
- 9. Lack of Contextual Awareness
Without contextual awareness, security teams may not fully understand the nature and potential impact of a threat, leading to ineffective responses. CTEM provides contextual insights by correlating threat data with business context, helping security teams understand the potential impact on critical assets and operations.
- 10. Slow Incident Response Times
Delays in detecting and responding to threats can lead to prolonged exposure and increased damage. By continuously monitoring and providing real-time alerts, CTEM enables faster detection and response to threats, minimizing the window of exposure.
- 11. Inadequate Threat Hunting Capabilities
Many organizations lack the tools and expertise to proactively hunt for threats within their environment. CTEM enhances threat hunting capabilities by providing advanced analytics, machine learning, and automation to identify and investigate potential threats.
- 12. Difficulty in Measuring Security Effectiveness
Organizations often struggle to measure the effectiveness of their security programs and demonstrate ROI to stakeholders. CTEM provides metrics and reporting capabilities that help organizations measure the effectiveness of their security efforts and demonstrate value to stakeholders.
By addressing these pain points, CTEM helps organizations build a more proactive, resilient, and adaptive cybersecurity posture, capable of responding to the evolving threat landscape effectively.
Why Traditional Security Approaches Fall Short
Traditional security methods increasingly reveal their limitations in protecting organizations against modern cyber threats. As attack surfaces expand and threats grow more sophisticated, these conventional approaches expose critical vulnerabilities that demand a fundamental shift in security thinking.
The Reactive Security Gap
Conventional security tools operate primarily on a detect-and-respond model, identifying threats only after they’ve already penetrated an organization’s defenses. This reactive approach creates a dangerous window of opportunity for attackers.
According to IBM’s 2024 Cost of a Data Breach Report, organizations take an average of 204 days to identify a breach and an additional 73 days to contain it. This extended dwell time results in significantly higher costs.
Limited Visibility
Traditional vulnerability management relies heavily on scheduled scanning and periodic assessments, creating dangerous blind spots in today’s dynamic IT environments. These point-in-time assessments quickly become outdated, leaving security teams with an incomplete and potentially misleading view of their security posture.
Overwhelming Alert Fatigue
The average security operations center (SOC) receives thousands of alerts every day. This constant barrage of alerts leads to decreased analyst productivity, increased response times, and heightened risk of missing critical threats. More concerning, many security professionals admit to turning off or turning down alert systems due to notification overload, creating dangerous security gaps.
How does CTEM differ from traditional vulnerability management frameworks
CTEM represents a fundamental shift from a periodic, reactive approach to a continuous, proactive, and integrated strategy for managing vulnerabilities and threats. It leverages advanced technologies and a broader scope to provide a more comprehensive and effective security posture, aligning closely with business objectives and adapting to the evolving threat landscape.
Proactive vs. Reactive
Traditional vulnerability management is often reactive, focusing on identifying and mitigating vulnerabilities after they have been discovered. It typically involves periodic scans and assessments, which can leave gaps in security between scans. CTEM is proactive and continuous. It aims to identify and address vulnerabilities in real-time, ensuring that threats are managed as they emerge. This approach reduces the window of exposure and helps organizations stay ahead of potential attacks.
Scope and Coverage
Traditional frameworks usually focus on known vulnerabilities within the IT infrastructure, such as software flaws and misconfigurations. They often rely on databases like the Common Vulnerabilities and Exposures (CVE) list. CTEM expands the scope to include a broader range of threats, including unknown vulnerabilities, misconfigurations, and emerging threats. It also considers the context of the business, such as the criticality of assets and the potential impact of a breach.
Integration and Automation
Traditional methods often involve manual processes and standalone tools. Integration with other security systems can be limited, leading to siloed information and slower response times.
CTEM emphasizes integration and automation. It leverages advanced technologies like AI, machine learning, and automation to continuously monitor, analyze, and respond to threats. This integration allows for a more cohesive and efficient security posture.
Risk Prioritization
Traditional frameworks typically prioritize vulnerabilities based on severity scores (e.g., CVSS scores) without always considering the specific context of the organization.
CTEM takes a more nuanced approach to risk prioritization. It considers factors such as the business impact, threat intelligence, and the likelihood of exploitation. This helps organizations focus on the most critical risks that could affect their operations.
Continuous Improvement
Traditional vulnerability management often follows a cyclical process (e.g., quarterly scans) with limited feedback loops for continuous improvement. CTEM is built on the principle of continuous improvement. It involves ongoing assessment, adaptation, and refinement of security practices based on real-time data and evolving threat landscapes.
Threat Intelligence
Traditional frameworks may not always align closely with business objectives, focusing more on technical vulnerabilities. CTEM aligns closely with business goals and risk appetite. It ensures that security measures are in place to protect critical assets and support business continuity.
The Six Pillars of CTEM
CTEM is a structured, ongoing process that enables security teams to systematically identify, assess, and mitigate security risks before adversaries exploit them. By following these six critical stages—Discover, Detect, Prioritize, Validate, Enroll, and Test—organizations can gain a comprehensive view of their attack surface and strengthen their security posture.
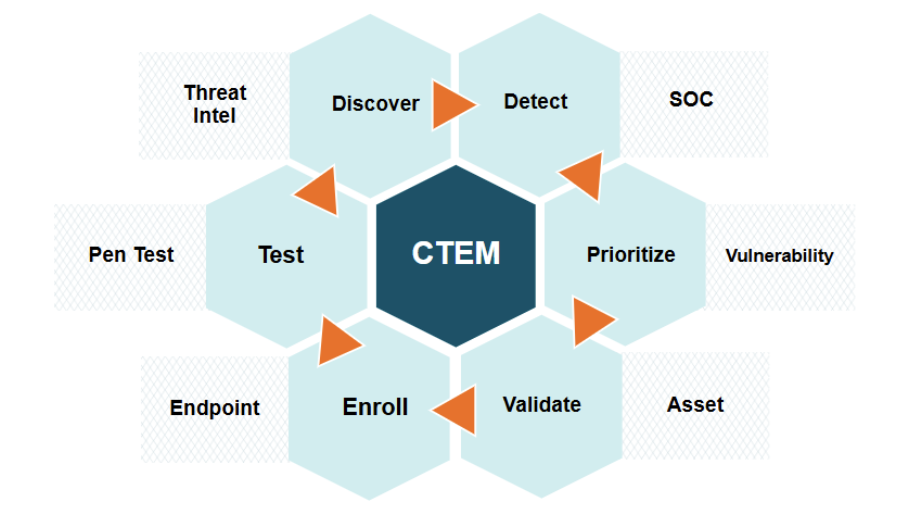
- 1. Discover: Mapping the Full Attack Surface
Effective threat exposure management begins with full visibility. Security teams must continuously map all digital assets, including on-premises systems, cloud environments, IoT devices, and third-party integrations. Shadow IT, misconfigured cloud services, and unmonitored endpoints often serve as entry points for cyber threats. By leveraging automated asset discovery tools and attack surface management solutions, organizations can ensure nothing falls through the cracks.
- 2. Detect: Identifying Vulnerabilities and Threats
Once assets are mapped, the next step is detecting vulnerabilities and potential threats. This involves leveraging threat intelligence, vulnerability scanners, and behavioral analytics to identify weaknesses that adversaries could exploit. Security teams should integrate real-time threat feeds and AI-driven anomaly detection to recognize zero-day vulnerabilities and sophisticated attack vectors before they escalate.
- 3. Prioritize: Focusing on the Most Critical Risks
Not all vulnerabilities pose the same level of risk. Prioritization ensures that security teams focus on the threats with the highest potential impact. By assessing risk based on exploitability, business impact, and threat actor activity, organizations can allocate resources effectively. Integrating risk-based vulnerability management (RBVM) frameworks enhances decision-making, ensuring security efforts align with business objectives.
- 4. Validate: Assessing Real-World Exploitability
Validating vulnerabilities is essential to eliminate false positives and understand the true exploitability of a security gap. Penetration testing, breach and attack simulations (BAS), and adversary emulation techniques provide security teams with actionable insights. This phase confirms whether identified vulnerabilities can be exploited in real-world attack scenarios, allowing organizations to prioritize remediation efforts accordingly.
- 5. Enroll: Implementing Mitigation and Security Controls
Addressing identified risks requires more than patching—it demands a strategic approach to security control implementation. Organizations must enroll security teams, IT administrators, and executive leadership in the remediation process. Automating security workflows, enforcing least-privilege access policies, and integrating security orchestration, automation, and response (SOAR) solutions help ensure timely risk mitigation.
- 6. Test: Continuously Validating Security Posture
Cyber threats evolve rapidly, and security measures must be tested continuously to remain effective. Regular penetration testing, red teaming, and continuous monitoring help organizations measure the effectiveness of their defenses. By adopting a continuous security validation approach, organizations can proactively identify weaknesses and adapt their security strategy to emerging threats.
The Business Impact of CTEM Implementation
Organizations that adopt CTEM not only improve their ability to withstand cyber threats, they also gain a competitive edge by demonstrating strong security governance to customers, partners, and stakeholders.
Enhanced Risk Reduction and Resilience
CTEM enables security teams to identify, prioritize, and remediate vulnerabilities before they can be exploited. Unlike periodic assessments, CTEM provides real-time visibility into an organization’s attack surface, reducing the likelihood of breaches that could lead to financial losses, reputational damage, and regulatory penalties.
Operational Efficiency and Cost Savings
By integrating CTEM into security operations, organizations eliminate redundant manual processes and focus on high-impact threats. This not only reduces time wasted on low-risk vulnerabilities but also optimizes resource allocation, cutting down on unnecessary security expenditures. The automation and continuous monitoring capabilities of CTEM further streamline workflows, enabling security teams to operate with greater precision and agility.
Regulatory Compliance and Audit Readiness
With cyber regulations becoming more stringent, businesses must demonstrate continuous risk management practices. CTEM helps organizations align with compliance frameworks such as NIST, ISO 27001, and CIS Controls by providing verifiable security data and actionable insights. This proactive stance minimizes compliance risks, reduces audit burdens, and ensures regulatory readiness.
Competitive Advantage
By implementing CTEM, businesses can assure customers, partners, and stakeholders that their data is protected against emerging threats. This trust enhances brand reputation, facilitates business partnerships, and ensures long-term operational stability.
Implementing CTEM: A Practical Approach
To implement CTEM effectively, security leaders must adopt a structured, data-driven approach that integrates seamlessly into existing security frameworks.
- 1. Establish a Continuous Risk Assessment Framework
A successful CTEM program starts with continuous risk assessment. Traditional, periodic security assessments leave dangerous visibility gaps. Instead, organizations must adopt an always-on approach that dynamically evaluates their attack surface. Leverage automated threat intelligence tools, vulnerability management platforms, and external attack surface monitoring to identify potential threats before they become incidents.
- 2. Prioritize Risks Based on Business Impact
Not all vulnerabilities pose the same level of risk. Prioritization is critical. Security teams should assess exposure based on exploitability, potential impact, and alignment with adversary tactics (such as those outlined in the MITRE ATT&CK framework). By integrating threat intelligence and real-world attack scenarios, organizations can focus resources on mitigating the most pressing risks.
- 3. Automate Threat Detection and Response
Manual processes cannot keep up with the speed of modern cyber threats. Implementing automation within Security Operations Centers (SOCs) enhances detection, investigation, and response capabilities. Security Orchestration, Automation, and Response (SOAR) platforms and Extended Detection and Response (XDR) solutions streamline workflows, reducing mean time to detect (MTTD) and respond (MTTR) to threats.
- 4. Integrate CTEM into Your Cybersecurity Strategy
CTEM should not operate in isolation. It should be aligned with existing security frameworks such as NIST Cybersecurity Framework, ISO 27001, and Zero Trust Architecture. This ensures that CTEM enhances—rather than disrupts—ongoing security initiatives. Additionally, integrating CTEM with cloud security posture management (CSPM) and identity threat detection and response (ITDR) strengthens protection across hybrid environments.
- 5. Measure, Adapt, and Improve
CTEM is a continuous process that requires ongoing optimization. Establish key performance indicators (KPIs) such as risk reduction over time, incident response effectiveness, and adversary dwell time. Use security analytics to refine detection models and enhance proactive defenses. Regular testing, such as red teaming and breach-and-attack simulations, validates the effectiveness of security controls.
Why Ascent Solutions is your Continuous Threat Exposure Management Partner of Choice
Ascent delivers a robust, multi-layered framework to identify and remediate security vulnerabilities across your entire infrastructure. Through five integrated services, we provide unparalleled visibility into your security posture:
Cyber Threat Intelligence as a Service (CTIaaS)
Cyber Threat Intelligence as a Service (CTIaaS) provides organizations with actionable insights and information about potential or current cyber threats. By subscribing to CTIaaS, you gain access to real-time, actionable intelligence that cuts through the noise of countless global threats to spotlight what matters most to your organization.
These services don’t just tell you what’s happening – they tell you why it matters and what to do about it. Whether it’s identifying the digital fingerprints of an attack (IoCs), unmasking the tactics of sophisticated threat actors, or spotting vulnerabilities before attackers can exploit them, CTIaaS provides the strategic advantage your organization needs.
Behind the scenes, specialized providers harness cutting-edge tools and extensive threat feeds, combined with human expertise, to build a comprehensive picture of your threat landscape. They customize their intelligence gathering to your specific industry, infrastructure, and security concerns, ensuring you receive insights that are relevant and actionable.
This targeted approach empowers your team to make confident security decisions and respond swiftly to incidents, all while avoiding the substantial investment required to build and maintain an internal threat intelligence capability.
Threat and Vulnerability Management as a Service (TVMaaS)
Threat and Vulnerability Management as a Service (TVMaaS) is your organization’s frontline defense against cyber threats. This fully managed security solution continuously identifies, assesses, and prioritizes vulnerabilities across your IT infrastructure—so you can stay ahead of attackers instead of reacting to them.
With 24/7 monitoring, real-time vulnerability scanning, and expert-driven risk assessments, TVMaaS delivers clear, actionable insights to strengthen your security posture. Powered by automation, advanced threat intelligence, and seasoned security professionals, it minimizes risk exposure while ensuring compliance with industry regulations.
Delivered as a flexible, subscription-based service, TVMaaS takes the complexity out of
cybersecurity, allowing your team to focus on business growth while trusted experts
handle your threat and vulnerability management.
cybersecurity, allowing your team to focus on business growth while trusted experts
handle your threat and vulnerability management.
Asset Management as a Service (AMaaS)
Asset Management as a Service (AMaaS) provides organizations with a comprehensive, outsourced solution for identifying, tracking, and securing their digital assets—including hardware, software, networks, and data. By leveraging AMaaS, organizations can ensure their assets remain protected, compliant with regulatory requirements, and optimized for operational efficiency.
By adopting AMaaS, organizations gain access to specialized expertise, advanced security tools, and continuous monitoring, enabling them to mitigate cyber risks more effectively while allowing internal teams to focus on strategic business initiatives. This proactive approach not only enhances security but also ensures compliance, operational efficiency, and long-term resilience against emerging threats.
Endpoint Management as a Service (EMaaS)
Endpoint Management as a Service (EMaaS) revolutionizes how businesses manage and secure their devices—laptops, desktops, mobile devices, and servers—without the hassle of on-premises infrastructure. This cloud-powered solution provides a centralized platform for seamless remote management, security enforcement, and compliance adherence.
With EMaaS, providers take care of critical tasks like software updates, security patches, and device provisioning, ensuring your endpoints stay protected and up to date. Built for scalability, it enables businesses to streamline IT operations, reduce costs, and support remote or hybrid workforces with ease.
Key benefits include automated patch management, real-time monitoring, remote troubleshooting, and robust endpoint security—all designed to enhance efficiency and fortify cybersecurity. Whether you’re a growing startup or an enterprise, EMaaS simplifies IT management so you can focus on what truly matters: driving your business forward.
Penetration Testing as a Service (PTaaS)
Penetration Testing as a Service (PTaaS) provides organizations with a proactive, continuous approach to security testing. Unlike traditional penetration testing, which is typically a one-time engagement, PTaaS delivers ongoing, on-demand security assessments to help organizations identify and remediate vulnerabilities in real-time.
This scalable model adapts to an organization’s changing needs, ensuring that security remains a constant priority rather than an occasional check-up. Beyond enhanced protection, PTaaS is also cost-effective, offering subscription-based pricing that provides predictable budgeting without compromising on quality.
By leveraging cutting-edge tools and specialized expertise, organizations gain deeper visibility into their security posture—without the burden of managing the process internally. With PTaaS, security becomes a continuous effort, empowering businesses to proactively mitigate risk, maintain compliance, and stay ahead of cyber threats in an increasingly complex digital environment.
Security Operations Center as a Service (SOCaaS)
Security Operations Center as a Service (SOCaaS) is a managed security solution that delivers continuous threat monitoring, detection, and response without the need for an in-house SOC team. Operating on a subscription-based model, SOCaaS gives organizations access to advanced cybersecurity expertise, real-time threat intelligence, and cutting-edge security tools—eliminating the need for costly infrastructure and dedicated personnel.
This solution is especially valuable for small to mid-sized businesses that lack the resources to maintain an internal SOC but still require enterprise-level security. One of its key benefits is 24/7 security monitoring and rapid incident response, minimizing the time needed to detect and contain cyber threats. By outsourcing security operations to experts, businesses can focus on their core objectives while ensuring their assets, data, and reputation remain protected.
Take Your CTEM Journey to the Next Level
As cyber threats continue to evolve in sophistication and frequency, organizations can no longer rely on point-in-time security assessments. Continuous Threat Exposure Management represents a fundamental shift in how enterprises approach cybersecurity – from reactive defense to proactive, continuous discovery and response.
Successfully implementing CTEM requires more than just tools; it demands expertise, proven methodologies, and a partner who understands your unique security landscape. With our comprehensive CTEM framework, industry-leading expertise, and track record of securing enterprises across diverse sectors, we provide the strategic guidance and technical capabilities needed to:
- Transform your security posture from periodic to continuous
- Identify and remediate exposures before they become breaches
- Optimize security resources through automated discovery and prioritization
- Demonstrate measurable risk reduction to stakeholders
Ready to Elevate Your Security Posture?
Don’t wait for a breach to expose your vulnerabilities. Partner with Ascent Solutions to
implement a robust CTEM program that keeps your organization ahead of emerging
threats.
Contact us today for a comprehensive assessment of your current security posture and
learn how our tailored approach can strengthen your cyber defense strategy.
implement a robust CTEM program that keeps your organization ahead of emerging
threats.
Contact us today for a comprehensive assessment of your current security posture and
learn how our tailored approach can strengthen your cyber defense strategy.
